During an incident response process performed in our client’s website, one of our analysts found a very interesting web shell. Our tools detected a suspicious file called “./v8.php” and after some time decoding it, we found out that it was a backdoor giving full shell access to the attackers.
The shell itself is very similar to the well known c99 webshell in which provides a variety of commands to manipulate the victim’s website (file structure) and database, also allowing him to execute commands the start malicious campaigns.
First, the encoded malware had an interesting comment at the top of the file:
"This file is protected by copyright law and provided under license. Reverse engineering of this file is strictly prohibited."
Attackers usually use that technique in order to somewhat avoid detection and further investigation from a suspicious eye.
What was so interesting about it? Well… how it was named: “<title> SEU MADRUGA Shell Recoded </title>”.
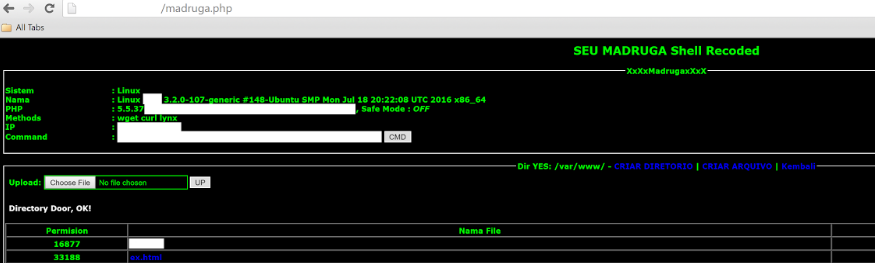
This (and this note’s title) may not seem to be funny for anyone outside latin America, so let me explain: “Seu Madruga” or “Don Ramón”, as the character is originally called, is one of the characters from a 1970’s Mexican super popular TV show called “El Chavo del Ocho”. This show was translated to portuguese and other 49 different languages and it is still very popular in Brazil, I would risk to say that every brazilian knows who “Seu Madruga” is, even if they weren’t big fans of the show. And the note’s title is based on one of his famous quotes.
So, when I saw that shell, this is the face that instantly came to my mind:

“Seu Madruga”, an unemployed former boxer who gets beat up by a lady almost daily can now be found on your site. So, as we always say, keep your website update, always check the core files, use a monitoring system to keep an eye on everything and make sure to have your website behind a firewall.
This post was also published at Sucuri Labs: http://labs.sucuri.net/?note=2016-08-24